Embark on a journey into the realm of Cloud security solutions, where the digital guardians of your data reside. Let’s explore how these solutions shield your information from cyber threats and ensure peace of mind in the digital age.
As we delve deeper, you’ll uncover the inner workings of cloud security solutions, unraveling the mysteries of encryption, access control, and more.
Introduction to Cloud Security Solutions
Cloud security solutions refer to a set of technologies, practices, and policies designed to protect data, applications, and infrastructure in cloud environments. These solutions help organizations secure their sensitive information and maintain the integrity and confidentiality of their data stored in the cloud.Implementing cloud security solutions is crucial for safeguarding against various cyber threats and vulnerabilities that can compromise the security of cloud-based resources.
By adopting these solutions, organizations can ensure data privacy, prevent unauthorized access, and mitigate the risks associated with cloud computing.
Examples of Common Threats Mitigated by Cloud Security Solutions
- Data Breaches: Cloud security solutions can help prevent unauthorized access to sensitive data stored in the cloud, reducing the risk of data breaches.
- Malware Attacks: By implementing cloud security measures such as antivirus software and intrusion detection systems, organizations can protect their cloud infrastructure from malware attacks.
- DDoS Attacks: Cloud security solutions can mitigate Distributed Denial of Service (DDoS) attacks by monitoring network traffic and blocking malicious traffic before it reaches the cloud resources.
- Insider Threats: Cloud security solutions include access controls and monitoring tools that can detect and prevent insider threats, such as unauthorized access by employees or contractors.
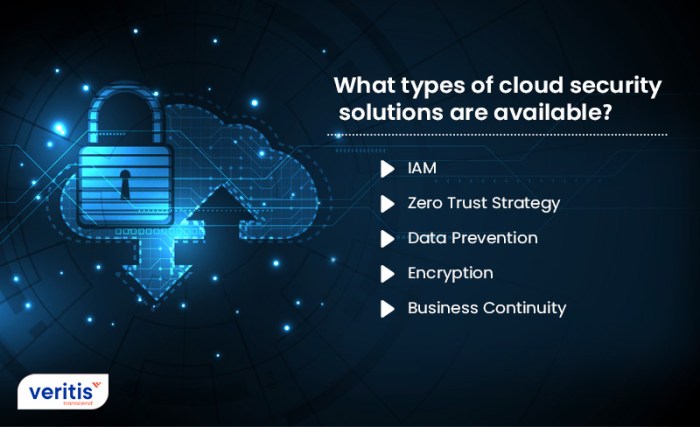
Types of Cloud Security Solutions
When it comes to safeguarding cloud environments, there are various types of cloud security solutions available in the market. These solutions offer different approaches to ensure the security and integrity of data stored in the cloud. Let’s explore some of the key types of cloud security solutions and their benefits.
Firewalls
Firewalls are a fundamental component of cloud security solutions. They act as a barrier between a trusted internal network and untrusted external networks, monitoring and controlling incoming and outgoing network traffic. Firewalls help prevent unauthorized access to cloud resources and protect against cyber threats.
Encryption
Encryption plays a crucial role in securing data in the cloud. By encoding information in a way that only authorized parties can access it, encryption helps protect sensitive data from unauthorized access or theft. Implementing encryption in cloud storage and communication channels adds an extra layer of security to prevent data breaches.
Intrusion Detection and Prevention Systems (IDPS)
IDPS solutions are designed to monitor network and system activities for malicious activities or policy violations. These systems can detect and respond to security threats in real-time, helping organizations identify and mitigate potential risks to their cloud infrastructure. By combining intrusion detection and prevention capabilities, IDPS solutions offer comprehensive security monitoring.
Multi-factor Authentication
Multi-factor authentication (MFA) is a security mechanism that requires users to provide two or more forms of verification before granting access to cloud resources. By adding an extra layer of authentication beyond passwords, MFA helps prevent unauthorized access even if login credentials are compromised. This reduces the risk of unauthorized access to sensitive data stored in the cloud.
Security Information and Event Management (SIEM)
SIEM solutions combine security information management (SIM) and security event management (SEM) to provide real-time analysis of security alerts generated by applications and network hardware. SIEM solutions help organizations detect and respond to security incidents promptly, allowing them to proactively address potential threats to their cloud environment.
Benefits of Using a Combination of Cloud Security Solutions
By combining various types of cloud security solutions, organizations can create a robust security posture that addresses different aspects of cloud security. Each type of security solution offers unique capabilities to protect against specific threats, and by leveraging a combination of these solutions, organizations can enhance their overall security posture. This multi-layered approach to cloud security helps mitigate risks and ensures the confidentiality, integrity, and availability of data in the cloud.
Components of Effective Cloud Security Solutions
In order to ensure robust protection of data in the cloud, there are key components that make up an effective cloud security solution. These components work together to create a secure environment for storing and accessing sensitive information.
Encryption in Cloud Security
Encryption is a crucial component of cloud security solutions as it helps to protect data by converting it into a format that is unreadable without the proper decryption key. This ensures that even if unauthorized users gain access to the data, they will not be able to make sense of it. Encryption helps to safeguard data both in transit and at rest, providing an additional layer of security for sensitive information.
- Encryption algorithms such as AES (Advanced Encryption Standard) are commonly used to secure data in the cloud.
- End-to-end encryption ensures that data is encrypted from the point of origin to the destination, preventing interception of sensitive information.
- Proper key management is essential to ensure that encryption keys are protected and only accessible to authorized users.
Access Control Mechanisms in Cloud Security
Access control mechanisms play a critical role in cloud security by regulating who can access data and resources within the cloud environment. By setting granular access controls, organizations can limit the exposure of sensitive information and prevent unauthorized access to critical systems.
- Role-based access control (RBAC) assigns permissions based on the roles and responsibilities of users, ensuring that they only have access to the resources they need to perform their tasks.
- Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification before accessing the cloud environment.
- Audit logs track and monitor user activities within the cloud platform, allowing organizations to detect and investigate any unauthorized access attempts.
Best Practices for Implementing Cloud Security Solutions

Implementing cloud security solutions is crucial for organizations to protect their data and systems from cyber threats. Here are some best practices to follow:
Establish a Comprehensive Security Strategy
- Define clear security objectives and requirements based on the organization’s needs.
- Develop a comprehensive security policy that Artikels roles, responsibilities, and procedures for ensuring data protection.
- Implement security controls and measures to safeguard cloud infrastructure and applications.
- Regularly review and update security policies to address evolving threats and vulnerabilities.
Ensure Compliance with Industry Standards
- Stay informed about industry regulations and standards related to data security and privacy.
- Implement security measures that align with industry best practices and compliance requirements.
- Regularly assess and audit security controls to ensure compliance with regulations such as GDPR, HIPAA, or PCI DSS.
- Engage with compliance experts and consultants to stay updated on regulatory changes and requirements.
Conduct Regular Security Audits and Assessments
- Perform regular security audits to identify vulnerabilities and weaknesses in the cloud environment.
- Conduct penetration testing and vulnerability assessments to proactively identify and mitigate security risks.
- Review access controls and user permissions to prevent unauthorized access to sensitive data.
- Monitor security logs and alerts to detect and respond to security incidents in a timely manner.
Security in Multi-Cloud Environments
In today’s digital landscape, many organizations are adopting a multi-cloud strategy to leverage the benefits of different cloud providers. However, securing data in multi-cloud environments poses unique challenges that need to be addressed effectively.One of the key challenges of securing data in multi-cloud environments is the complexity of managing security across multiple platforms. Each cloud provider may have its own security protocols, making it difficult to ensure consistent protection of data.
Strategies for Ensuring Consistent Security
- Implementing a centralized security management system that can monitor and control security policies across all cloud platforms.
- Utilizing encryption techniques to protect data both at rest and in transit, regardless of the cloud provider.
- Regularly auditing and assessing the security posture of each cloud environment to identify and mitigate potential vulnerabilities.
Importance of Integration and Interoperability
- Integration of security solutions across multiple cloud platforms ensures seamless communication and coordination between different security tools.
- Interoperability allows for the exchange of security data and alerts between various cloud environments, enabling a more holistic approach to threat detection and response.
- By focusing on integration and interoperability, organizations can achieve a higher level of security effectiveness and reduce the risk of security gaps in their multi-cloud environments.
Ultimate Conclusion
In a digital landscape fraught with dangers, Cloud security solutions stand as stalwart protectors of your valuable data. With a blend of robust components, best practices, and strategies for multi-cloud environments, your information remains safe and sound.
User Queries
What are some common threats that cloud security solutions can mitigate?
Cloud security solutions can help prevent data breaches, DDoS attacks, malware infections, and unauthorized access to sensitive information.
How does encryption play a role in securing data in the cloud?
Encryption scrambles data into an unreadable format, ensuring that even if intercepted, the information remains protected from prying eyes.
Why is regular security auditing important for maintaining cloud security?
Regular security audits help identify vulnerabilities, assess compliance with regulations, and ensure that security measures are up to date to combat evolving threats.