Step into the future of cybersecurity with a glimpse into 2025, where new technologies and threats collide in a digital battleground. Get ready for an eye-opening journey ahead!
As we delve deeper, we’ll uncover the key factors shaping cybersecurity trends, from emerging technologies to potential challenges on the horizon.
Cybersecurity Trends 2025
In 2025, the cybersecurity landscape is expected to be more complex and challenging than ever before. With the rapid advancement of technology, organizations will need to adapt and evolve their cybersecurity practices to stay ahead of cyber threats.
Predicted Key Factors Influencing Cybersecurity Trends
- The increasing use of artificial intelligence and machine learning in cybersecurity defenses.
- The rise of quantum computing posing a threat to traditional encryption methods.
- The growing interconnectedness of devices in the Internet of Things (IoT) leading to more attack surfaces.
Emerging Technologies Shaping Cybersecurity Practices
- Zero Trust security model becoming more prevalent to verify every user and device trying to access the network.
- Biometric authentication and behavioral analytics for enhanced identity verification.
- Blockchain technology for secure data storage and transactions.
Potential Challenges and Threats for Organizations
- Ransomware attacks becoming more sophisticated and widespread, targeting critical infrastructure.
- Increased regulations and compliance requirements impacting cybersecurity strategies.
- A shortage of skilled cybersecurity professionals leading to gaps in defense capabilities.
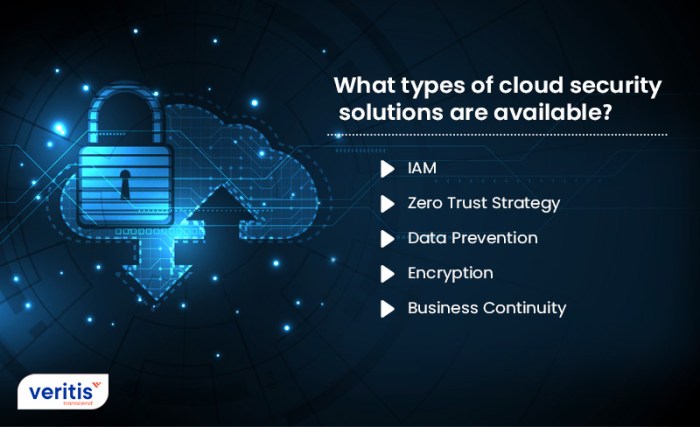
Security Measures

In today’s digital landscape, the protection of sensitive data and information is of paramount importance. Various security measures are in place to combat cyber threats and ensure the safety of personal and organizational data.Encryption plays a crucial role in safeguarding sensitive information. By converting data into a code that can only be deciphered by authorized parties, encryption helps prevent unauthorized access and protects data from being intercepted or tampered with during transmission.Multi-factor authentication is another key security measure that enhances security protocols.
By requiring users to provide multiple forms of verification before granting access, such as a password, fingerprint scan, or security token, multi-factor authentication adds an extra layer of protection against unauthorized access attempts.
Traditional vs Modern Security Methods
- Traditional security methods often rely on perimeter defenses, such as firewalls and antivirus software, to protect against cyber threats. While still important, these methods are no longer sufficient in today’s complex threat landscape.
- Modern approaches to security focus on proactive threat detection and response, utilizing technologies like artificial intelligence and machine learning to identify and mitigate potential security risks in real-time.
- Continuous monitoring and security assessments are also key components of modern security strategies, ensuring that systems are regularly evaluated for vulnerabilities and weaknesses.
Importance of Encryption
- Encryption is essential for protecting sensitive data, such as financial information, personal details, and intellectual property, from unauthorized access.
- By encrypting data at rest and in transit, organizations can maintain confidentiality and integrity, even if the data is intercepted or stolen.
- End-to-end encryption, where data is encrypted from the sender to the recipient, ensures that only authorized parties can access the information.
Role of Multi-Factor Authentication
- Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification before accessing sensitive information or systems.
- Common factors used in multi-factor authentication include something the user knows (like a password), something the user has (like a security token), and something the user is (like a fingerprint or facial recognition).
- By implementing multi-factor authentication, organizations can significantly reduce the risk of unauthorized access and data breaches, even if login credentials are compromised.
Closing Notes

In conclusion, Cybersecurity trends 2025 paint a picture of a rapidly evolving landscape where vigilance and innovation are paramount. Stay ahead of the curve and brace yourself for what’s to come in the world of digital security.
FAQ
What are some unique cybersecurity challenges expected in 2025?
With the rise of AI and IoT, protecting interconnected devices and systems will be a major challenge.
How will emerging technologies impact cybersecurity practices by 2025?
Technologies like quantum computing and AI will revolutionize security protocols and threat detection.
Why is encryption essential for safeguarding sensitive information?
Encryption ensures that data is secure and unreadable to unauthorized users, maintaining confidentiality.
What role does multi-factor authentication play in enhancing security?
Multi-factor authentication adds an extra layer of security by requiring multiple forms of verification, reducing the risk of unauthorized access.