With Network security threats at the forefront, get ready to dive into the wild world of cybersecurity where every click could be a potential threat. From sneaky hackers to malicious malware, this journey will be a rollercoaster of information and strategies to keep your networks safe and sound.
Let’s uncover the lurking dangers and arm ourselves with the knowledge to protect against the unseen threats that could jeopardize the integrity of our digital domains.
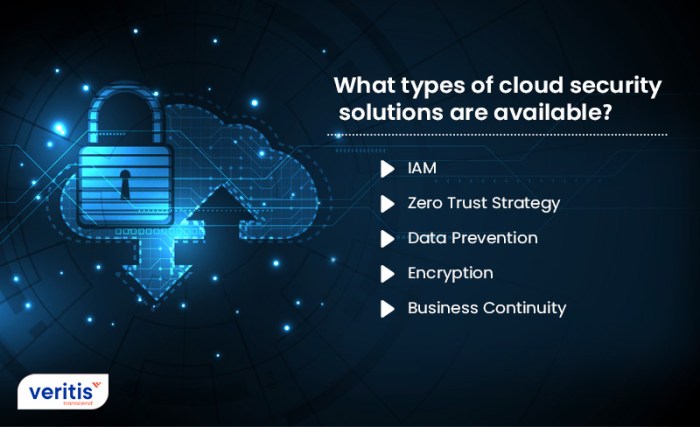
Network Security Threats
Network security threats pose significant risks to organizations, as hackers continuously exploit vulnerabilities to gain unauthorized access to sensitive data and disrupt operations.
Common Types of Network Security Threats
- Malware: Malicious software designed to damage or gain unauthorized access to computer systems.
- Phishing: Deceptive emails or websites used to trick users into revealing sensitive information.
- Denial of Service (DoS) Attacks: Overloading a network with traffic to disrupt services and make them unavailable.
- Man-in-the-Middle Attacks: Interception of communication between two parties to steal data.
Impact of Network Security Threats on Organizations
- Financial Loss: Data breaches and downtime can lead to significant financial losses for organizations.
- Reputation Damage: Security incidents can tarnish the reputation of an organization, leading to loss of trust from customers and partners.
- Legal Consequences: Failure to protect data can result in legal penalties and regulatory fines.
Methods Used by Hackers to Exploit Network Vulnerabilities
- Scanning: Hackers use scanning tools to identify vulnerabilities in a network that can be exploited.
- Brute Force Attacks: Attempting to guess passwords or encryption keys to gain unauthorized access.
- Packet Sniffing: Monitoring network traffic to capture sensitive information such as passwords or credit card details.
Malware Attacks

Malware attacks are a common threat to network security, with cybercriminals using various types of malicious software to infiltrate and compromise systems. These attacks can have devastating consequences, ranging from data breaches to financial losses and reputational damage. It is crucial for organizations to be aware of the different types of malware and implement effective strategies to prevent infections on their networks.
Examples of Malware
- Viruses: Self-replicating programs that attach themselves to clean files and spread when the infected files are executed.
- Trojans: Malware disguised as legitimate software to trick users into installing them, allowing cybercriminals to gain unauthorized access to systems.
- Ransomware: Malware that encrypts files or locks users out of their systems until a ransom is paid, often causing significant disruptions to operations.
- Spyware: Malware that secretly collects sensitive information from users without their knowledge, such as login credentials or financial data.
Consequences of Malware Attacks
- Data Loss: Malware attacks can result in the loss of sensitive data, leading to financial and legal consequences for organizations.
- Financial Damage: Ransomware attacks can demand large sums of money in exchange for decrypting files, causing financial strain on businesses.
- Reputational Harm: A successful malware attack can damage an organization’s reputation and erode customer trust, leading to long-term consequences.
Preventing Malware Infections
- Install Antivirus Software: Use reputable antivirus programs to detect and remove malware from systems.
- Keep Software Updated: Regularly update operating systems and applications to patch security vulnerabilities that malware can exploit.
- Be Cautious with Email Attachments: Avoid opening attachments or clicking on links from unknown or suspicious sources to prevent malware infections.
- Implement Security Policies: Establish and enforce security policies such as strong password requirements and restricted access to sensitive data to mitigate the risk of malware attacks.
Phishing Schemes
Phishing schemes are a type of cyber attack where malicious actors impersonate legitimate organizations or individuals to trick users into revealing sensitive information such as login credentials, financial data, or personal details.Phishing attacks can take many forms, including email phishing, spear phishing, and pharming. Email phishing involves sending fraudulent emails that appear to be from a trusted source, while spear phishing targets specific individuals or organizations with personalized messages.
Pharming, on the other hand, redirects users to fake websites without their knowledge.
Types of Phishing Attacks
- Social Engineering: Phishing attacks often rely on social engineering tactics to manipulate users into divulging confidential information.
- Clone Phishing: In this type of attack, hackers create a replica of a legitimate email to deceive users into clicking on malicious links.
- Whaling: Whaling attacks target high-profile individuals within an organization, such as executives or CEOs, to gain access to sensitive data.
Training Program for Recognizing Phishing Attempts
Implementing a comprehensive training program is essential to educate employees on how to recognize and respond to phishing attempts. The program should include:
- Interactive Workshops: Conduct workshops that simulate real-world phishing scenarios to help employees identify red flags and avoid falling for scams.
- Regular Updates: Provide ongoing training sessions to keep employees informed about the latest phishing trends and tactics.
- Phishing Simulation Tools: Utilize phishing simulation tools to test employees’ awareness and provide feedback on their responses.
Data Breaches
Data breaches are a major concern in network security, as they can result in the unauthorized access, disclosure, or manipulation of sensitive information. These breaches can have serious repercussions for organizations, including financial losses, damage to reputation, and legal consequences.
Main Causes of Data Breaches
- Weak or stolen credentials: Hackers often exploit weak passwords or steal credentials to gain access to networks and sensitive data.
- Malware and ransomware attacks: Malicious software can be used to infect systems and steal data, or hold it hostage for ransom.
- Insider threats: Employees or contractors with access to sensitive information may intentionally or inadvertently cause a data breach.
- Phishing attacks: Cybercriminals use phishing emails to trick users into revealing sensitive information, such as login credentials.
Mitigation of Data Breach Risks
- Implementing strong security measures: Organizations can use encryption, multi-factor authentication, and regular security audits to protect sensitive data.
- Employee training: Providing cybersecurity awareness training to staff can help prevent data breaches caused by human error or negligence.
- Data backup and recovery: Regularly backing up data and having a solid recovery plan in place can help minimize the impact of a data breach.
- Monitoring and detection: Continuous monitoring of network activity and implementing intrusion detection systems can help identify and respond to data breaches quickly.
Long-term Consequences of Data Breaches
- Financial losses: Data breaches can result in significant financial costs, including legal fees, regulatory fines, and loss of customers.
- Reputation damage: Organizations that experience data breaches may suffer from a loss of trust from customers, partners, and stakeholders.
- Legal implications: Data breaches can lead to lawsuits, regulatory investigations, and compliance penalties, which can have lasting legal consequences for companies.
- Data breach disclosure requirements: Companies may be required to publicly disclose data breaches, which can further damage their reputation and erode customer trust.
Ultimate Conclusion

As we conclude our exploration into the realm of network security threats, remember that vigilance is key. Stay informed, stay prepared, and stay secure in the ever-evolving landscape of cybersecurity.
FAQ Explained
How can organizations detect network security threats effectively?
Implementing intrusion detection systems and regular security audits can help organizations stay ahead of potential threats.
What are some common signs of a malware infection on a network?
Suspicious pop-ups, slow network performance, and unauthorized file changes can indicate a malware presence.
How do phishing schemes exploit human vulnerabilities in network security?
Phishing schemes often rely on social engineering tactics to trick users into divulging sensitive information or clicking on malicious links.
What are the immediate steps to take in case of a data breach?
Isolating affected systems, notifying relevant parties, and conducting a thorough investigation are crucial initial steps after a data breach.
How can employees contribute to strengthening network security defenses?
Regular cybersecurity training, strong password practices, and awareness of potential threats can empower employees to be the first line of defense against network security threats.