Get ready to dive into the world of security automation tools where efficiency meets protection. Imagine a realm where your cybersecurity is fortified with automated processes, making your defenses impenetrable. Let’s explore the key to safeguarding your digital assets in the most innovative way possible.
Security Automation Tools Overview
Security automation tools are software solutions designed to streamline and enhance security processes within an organization. These tools are programmed to automate repetitive tasks, detect and respond to security incidents, and enforce security policies consistently.
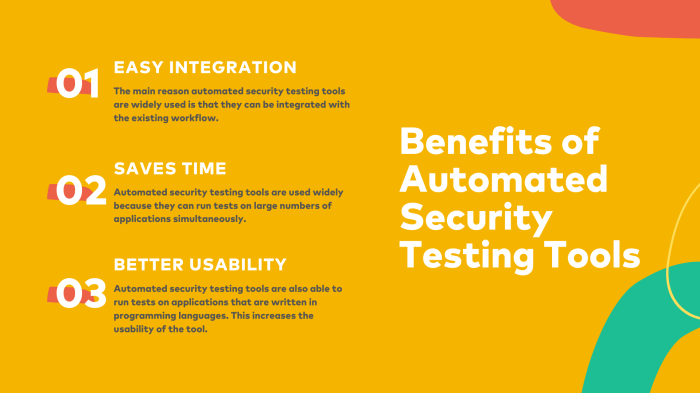
Key Benefits of Using Security Automation Tools
- Improved Efficiency: Security automation tools can perform tasks at a much faster pace than humans, leading to increased efficiency in security operations.
- Enhanced Accuracy: By automating security processes, the likelihood of human error is reduced, leading to more accurate results.
- Scalability: These tools can handle a large volume of security tasks simultaneously, allowing organizations to scale their security operations as needed.
- Cost Savings: Automation helps in reducing the need for manual labor, ultimately saving costs for the organization.
Importance of Integrating Automation in Security Practices
Integrating automation in security practices is crucial in today’s rapidly evolving threat landscape. By automating routine security tasks, organizations can free up their security teams to focus on more strategic activities such as threat analysis and incident response.
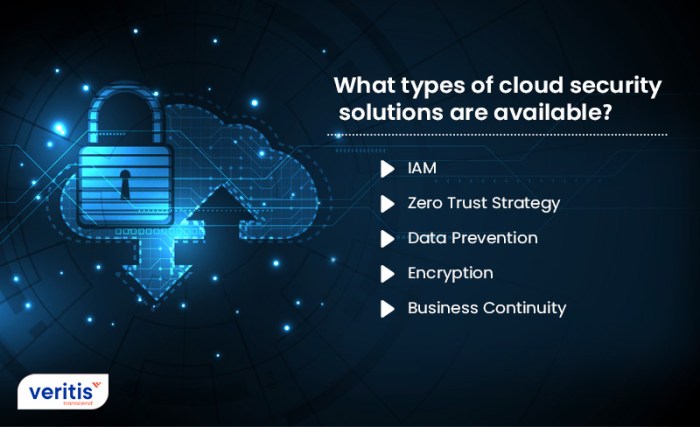
Types of Security Automation Tools
When it comes to security automation, there are various types of tools available to help organizations streamline their security processes and improve overall cybersecurity posture. Let’s explore some of the key categories of security automation tools below.
Vulnerability Scanners
Vulnerability scanners are tools designed to identify security vulnerabilities within an organization’s systems, networks, and applications. These tools scan the IT environment for known vulnerabilities, misconfigurations, and weaknesses that could be exploited by attackers. They provide detailed reports on the vulnerabilities found, prioritize them based on severity, and help security teams remediate the issues to reduce the attack surface.
SIEM Tools (Security Information and Event Management)
SIEM tools collect and analyze security event data from various sources across the organization, such as logs, network traffic, and endpoints. They help security teams detect and respond to security incidents in real-time by correlating and analyzing the data to identify potential threats. SIEM tools provide centralized visibility into the security posture of the organization, enable threat hunting, and support compliance requirements.
Automated Incident Response Tools
Automated incident response tools help organizations automate the process of responding to security incidents, such as malware infections, data breaches, and unauthorized access. These tools can automatically contain and mitigate threats, isolate affected systems, and initiate response actions based on predefined playbooks. Automated incident response tools help organizations reduce response times, minimize the impact of incidents, and improve overall incident handling efficiency.
Comparison of Open-Source vs. Commercial Security Automation Tools
Open-source security automation tools are typically free to use and provide flexibility for customization based on specific requirements. They are community-driven, allowing users to contribute to the development and improvement of the tools. On the other hand, commercial security automation tools often come with additional features, support, and maintenance services. They are backed by dedicated vendor support, regular updates, and integration with other security products.
Organizations need to consider factors such as budget, resources, and feature requirements when choosing between open-source and commercial security automation tools.
Implementing Security Automation Tools

Implementing security automation tools in an organization is crucial to streamline security processes, enhance efficiency, and strengthen overall security posture. Below is a step-by-step guide on how to successfully implement security automation tools.
Step-by-Step Guide
- 1. Identify Security Requirements: Begin by assessing your organization’s security needs and identifying areas where automation can be beneficial.
- 2. Research and Select Tools: Research different security automation tools available in the market and choose the ones that best align with your requirements.
- 3. Plan Implementation Strategy: Develop a detailed implementation plan outlining the deployment process, timeline, and responsible team members.
- 4. Configure Tools: Configure the selected security automation tools according to your organization’s security policies and requirements.
- 5. Test and Validate: Conduct thorough testing to ensure that the tools are properly configured and functioning as expected.
- 6. Train Personnel: Provide training to your team members on how to use the security automation tools effectively.
- 7. Monitor and Evaluate: Continuously monitor the performance of the tools and make necessary adjustments to optimize their functionality.
Best Practices for Configuration and Optimization
- 1. Regularly Update Tools: Ensure that the security automation tools are regularly updated with the latest patches and updates to address vulnerabilities.
- 2. Customize Rules and Policies: Tailor the rules and policies within the tools to suit your organization’s specific security requirements.
- 3. Integrate Tools: Implement integration between different security automation tools to create a cohesive security ecosystem.
- 4. Automate Routine Tasks: Automate repetitive and routine security tasks to free up time for your security team to focus on more critical issues.
Common Challenges and Solutions
- 1. Resistance to Change: Address resistance to change by involving key stakeholders in the decision-making process and highlighting the benefits of automation.
- 2. Lack of Skills: Provide training and upskilling opportunities to ensure that your team has the necessary skills to effectively use the security automation tools.
- 3. Integration Issues: Work closely with vendors and IT teams to resolve any integration issues that may arise during the implementation process.
- 4. Compliance Concerns: Ensure that the security automation tools comply with relevant regulations and standards to avoid compliance issues.
Ensuring Effectiveness of Security Automation Tools
Security automation tools play a crucial role in enhancing the overall security posture of an organization. However, it is essential to ensure that these tools are effective in detecting and responding to security incidents. Monitoring and measuring their effectiveness is key to maintaining a strong security infrastructure.
Strategies for Monitoring and Measuring Effectiveness
Monitoring and measuring the effectiveness of security automation tools can be achieved through various strategies:
- Regularly reviewing security incident reports generated by the automation tools to assess the number and severity of incidents detected.
- Conducting periodic penetration testing to evaluate the tools’ ability to detect and respond to simulated attacks.
- Implementing key performance indicators (KPIs) to track the efficiency and accuracy of the tools in identifying threats.
- Utilizing security information and event management (SIEM) systems to centralize monitoring and analysis of security alerts.
Integrating Automation Tools with Existing Security Infrastructure
Integrating security automation tools with the existing security infrastructure is essential for seamless operation and optimal effectiveness:
- Ensure compatibility and interoperability between the automation tools and other security solutions deployed within the organization.
- Establish clear communication channels between the automation tools and existing security systems to facilitate data sharing and response coordination.
- Regularly update and maintain the automation tools to align with any changes or updates in the overall security infrastructure.
Role of Human Intervention and Oversight
While security automation tools can significantly enhance the efficiency and speed of security incident response, human intervention and oversight are still crucial components:
- Human analysts play a vital role in interpreting and validating the alerts generated by the automation tools to avoid false positives or negatives.
- Security teams should provide ongoing training and supervision to ensure that automated processes are functioning correctly and in line with security policies.
- Human experts can investigate complex security incidents that require in-depth analysis and decision-making beyond the capabilities of automated tools.
Wrap-Up
As we conclude our journey through the realm of security automation tools, remember that staying ahead in cybersecurity is not just a choice but a necessity. Embrace automation, fortify your defenses, and navigate the digital landscape with confidence and resilience.
Top FAQs
How do security automation tools work?
Security automation tools automate tasks such as monitoring, incident response, and vulnerability assessments to enhance the overall security posture.
What are the benefits of using security automation tools?
Benefits include faster response times, reduced human error, scalability, and enhanced threat detection capabilities.
How can organizations implement security automation tools effectively?
Organizations can implement security automation tools by defining goals, selecting the right tools, training staff, and continuously monitoring and optimizing the tools.
What role does human intervention play in automated security processes?
Human intervention is crucial for decision-making, oversight, and handling complex security incidents that may require human judgment.